
News & Updates
 |
News & Updates |
||||
| Home | About | Specification | Papers & Presentations | Events | FAQ | Contact Us | |||||
Thor virus, a new threat under Locky�s ransomware umbrellaThis article highlights the essentials of the Thor virus, the latest variant of Locky file-encrypting plague that extorts Bitcoins for data recovery. |
Ransom Trojans have been haunting computer users for years, posing a multimillion-dollar underground economy that the law enforcement still cannot countervail efficiently. The individuals liable for this cryptography-backed extortion lurk behind several layers of anonymity propped by The Onion Router technology and the use of Bitcoin for financial transactions. The ransomware called Locky is a prime example of how fine-tuned this online racketeering can get. It freezes victims� files with unbeatable crypto and skillfully covers its tracks so that neither free decryption nor identification of the threat actors is feasible. The latest variant of Locky known as the Thor ransomware follows suit and even outperforms its four predecessors, namely Locky proper, Zepto, Odin, and the .sh*t extension version. 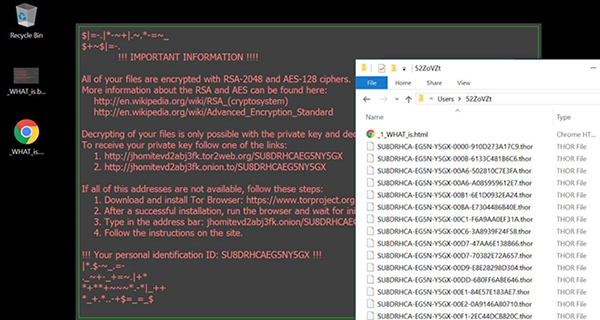
Thor surfaced in late October 2016. It got its name from the .thor file extension appended to a prey�s personal documents, videos, images, databases and other potentially valuable data. The only known way that this ransomware release propagates is via spam. The crooks employ a botnet-powered automated mailing service to generate thousands of phishing messages per day. The most widespread themes of these tricky emails include invoices, urgent payment requests, fax transmissions, payment history, detailed bills, e-tickets, order details, receipts, and complaint letters. The attachments are mainly ZIP archives with VBS, JS, HTA or DOCM files inside. The moment a recipient opens one of these files for whatever reason, they inadvertently expose their computer to a backstage compromise as the malicious script downloads all bits and pieces of the ransomware in a covert fashion. 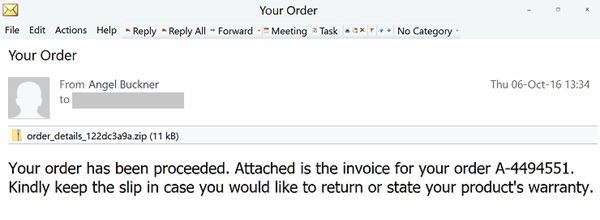
Once the breach has taken place, it�s not only the data on local hard drive volumes that�s at risk. Thor also traverses removable drives and network locations to find the victim�s important files. The criterion for determining whether or not an object should be encrypted is the extension thereof, the whitelist being embedded in the ransomware�s configuration file. Everything that meets the attackers� requirements in this context gets encrypted with RSA-2048 and AES-128 ciphers. Thor also cripples filenames, turning every entry into a string like TU7DRKBA-EHSR-Y4GX-00F4-0B9158A70811.thor. Consequently, it�s impossible to work out which file this object corresponds to. The Thor ransomware drops a couple of ransom notes to guide the infected users through the file decryption process. These files are called _WHAT_is.html, _[Random Number]_WHAT_is.html, and _WHAT_is.bmp. Furthermore, the desktop wallpaper changes to an image containing the same instructions and a unique ID. According to all of these manuals, the victim must visit the Locky Decryptor page and send 0.5 Bitcoin to a cryptocurrency wallet indicated there. In return, the bad guys claim to make the automatic decryption software available. Unfortunately, no one can ever be sure that the malefactors will do what they promise even after the payment is made. So it�s not recommended to go this route, at least not until you have tried everything else to restore your locked data. First check whether Thor has deleted the Shadow Copies of your files: right-click on an arbitrary object, select Properties, go to Previous Versions tab, and see if there are any backups listed there. If you are lucky, it may be possible to get around the cryptographic obstacle this way. Forensic utilities may be of help to revive the information as well. The best way to protect against Thor and other ransomware, though, is to ignore suspicious email attachments � as easy as that. Meanwhile, keep it in mind that secure data backups pose the most effective incident response strategy. |